Whoa, whoa, whoa… ein Newsletter-Dienstleister aus Deutschland, der mit Konformität zur DSGVO wirbt.
Ei, dann gucken wir doch mal:
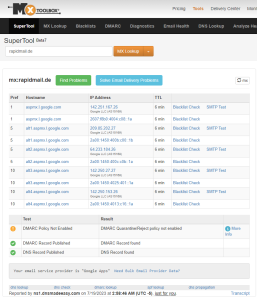
eigener MX-Eintrag von rapidmail.de
Boah, das sieht dann schon nicht so prickelnd aus, wenn man seine eigene Email-Infrastruktur bei Google abgibt.
Aber gucken wir doch mal weiter, wie sieht es denn mit den Datenschutzerklärungen aus:
https://www.rapidmail.de/datenschutz-kundenbereich
In der Version von heute, 19.07.2023:
Zusammenarbeit mit weiteren Auftragsverarbeitern und Dritten
Zur Erreichung der oben genannten Zwecke setzen wir Dienstleister als Auftragsverarbeiter gemäß Art. 28 DSGVO ein, etwa als IT-Dienstleister, zum Versand von E-Mails und SMS oder zur Kontaktaufnahme per Telefon. Diese Dienstleister können Ihren Sitz sowohl innerhalb als auch außerhalb der Europäischen Union bzw. des Europäischen Wirtschaftsraumes haben. Wir stellen durch vertragliche Vereinbarungen (sog. „Auftragsverarbeitungsvertrag“) mit den Dienstleistern sicher, dass diese personenbezogene Daten in Übereinstimmung mit den Vorgaben der DSGVO verarbeiten, auch wenn die Datenverarbeitung außerhalb der Europäischen Union bzw. des Europäischen Wirtschaftsraumes in Ländern stattfindet, in denen ein angemessenes Datenschutzniveau ansonsten nicht gewährleistet ist und für die kein Angemessenheitsbeschluss der Europäischen Kommission besteht. Für weitere Informationen über das Vorhandensein eines Angemessenheitsbeschlusses der Europäischen Kommission und über angemessene Garantien sowie um eine Kopie dieser Garantien zu erhalten, können Sie unseren Datenschutzbeauftragten kontaktieren. Darüber hinaus übermitteln wir Daten an Dritte nur, sofern dazu eine rechtliche Verpflichtung besteht. In diesem Fall beruht die Übermittlung auf Art. 6 Abs. 1 S. 1 lit. c) DSGVO.
Im Rahmen einer Verarbeitung in unserem Auftrag erbringt ein Drittanbieter für uns die Dienste zum Hosting und zur Darstellung der Plattform. Dies dient der Wahrung unserer im Rahmen einer Interessensabwägung überwiegenden berechtigten Interessen an einer korrekten Darstellung unseres Angebots.
Sofern wir Daten in einem Drittland (d.h. außerhalb der Europäischen Union (EU) oder des Europäischen Wirtschaftsraums (EWR)) verarbeiten oder dies im Rahmen der Inanspruchnahme von Diensten Dritter oder Offenlegung, bzw. Übermittlung von Daten an Dritte geschieht, erfolgt dies nur, wenn es zur Erfüllung unserer (vor)vertraglichen Pflichten, auf Grundlage Ihrer Einwilligung, aufgrund einer rechtlichen Verpflichtung oder auf Grundlage unserer berechtigten Interessen geschieht. Vorbehaltlich gesetzlicher oder vertraglicher Erlaubnisse, verarbeiten oder lassen wir die Daten in einem Drittland nur beim Vorliegen der besonderen Voraussetzungen der Art. 44 ff. DSGVO verarbeiten. D.h. die Verarbeitung erfolgt z.B. auf Grundlage besonderer Garantien, wie der offiziell anerkannten Feststellung eines der EU entsprechenden Datenschutzniveaus oder Beachtung offiziell anerkannter spezieller vertraglicher Verpflichtungen (so genannte „Standardvertragsklauseln“).
Einsatz von Ticketsystem Helpscout
Beschreibung und Zweck
Wir verwenden das CRM- und Ticket-System Help Scout, betrieben von Help Scout Inc., 131 Tremont St, Boston, MA 02111-1338, USA, um Anfragen der Nutzer schneller und effizienter bearbeiten zu können. Help Scout nutzt die Daten der Nutzer nur zur technischen Verarbeitung der Anfragen und gibt sie nicht an Dritte weiter. Zur Verwendung von Help Scout ist mindestens die Angabe einer korrekten E-Mail-Adresse notwendig. Eine pseudonyme Nutzung ist möglich. Im Verlauf der Bearbeitung von Service-Anfragen kann es notwendig sein, dass weitere Daten erhoben werden (Name, Adresse). Wenn Nutzer mit einer Datenerhebung über und einer Datenspeicherung im externen System von Help Scout nicht einverstanden sind, bieten wir ihnen alternative Kontaktmöglichkeiten zur Einreichung von Service-Anfragen per E-Mail, Telefon, Telefax oder Post. Sofern Help Scout innerhalb einer Software-Lösung implementiert worden ist und unsere Kunden hieraus Service-Anfragen stellen, so werden die Anfragen automatisiert mit einer Lizenz- oder Kundennummer zugeordnet. Help Scout erfüllt einige Zertifizierungen, wie Privacy-Shield oder HIPAA.
Rechtsgrundlage
Rechtsgrundlage für die Verarbeitung von personenbezogenen Daten ist das berechtigte Interesse gem. Art. 6 Abs. 1 lit. f) DSGVO an der effizienten Bearbeitung der Anfragen unserer Kunden.
Empfänger
Empfänger ist Help Scout Inc., 131 Tremont St, Boston, MA 02111-1338, USA.
Ãœbermittlung an Drittstaaten
Eine Ãœbermittlung von Daten in die USA findet statt.
Dauer der Datenspeicherung
Die Daten werden gelöscht, sobald sie für die Erreichung des Zweckes ihrer Erhebung nicht mehr erforderlich sind. Darüber hinaus werden die Daten gelöscht, sofern Sie Ihre Einwilligung widerrufen bzw. die Löschung der personenbezogenen Daten verlangen.
Widerrufsmöglichkeit
Sie haben die Möglichkeit, Ihre Einwilligung zur Datenverarbeitung jederzeit zu widerrufen. Ein Widerruf wirkt sich auf die Wirksamkeit von in der Vergangenheit liegenden Datenverarbeitungsvorgängen nicht aus.
Vertragliche oder gesetzliche Pflicht
Es besteht keine vertragliche oder gesetzliche Pflicht für die Bereitstellung der Daten.
Weitere Datenschutzhinweise via Link
Nähere Informationen zu Datenverarbeitung und Datenschutz durch Help Scout finden Sie hier:
https://www.helpscout.com/company/legal/privacy/
Aber sicher doch, schön Daten in Drittländer schicken!
Komisch, da gabs doch was von Schrems aus 2020… ach was, das ist ja erst neulich durch einen anderen Bullshit wieder „legalisiert“ worden, wird DIESMAL SICHERLICH BESSER sein als davor.
(Spoiler: nope, same shit, different paper)
Okay, aber das is ja nur das Backend, wo man als Kunde seine Daten einkippt, das ist ja NICHT die Versende-Infrastruktur!
Ähm, ja, genau! DER Bereich, in dem zum ersten Mal die personenbezogenen Daten von mir zu jemand Anderem wechseln.
Und da darf dann natürlich auch das hier nicht fehlen:
Einsatz von Google Analytics Nutzertracking
Beschreibung und Zweck
Diese Website nutzt den Dienst „Google Analytics“, welcher von der Google LLC. (1600 Amphitheatre Parkway Mountain View, CA 94043, USA) angeboten wird, zur Analyse der Websitebenutzung durch Nutzer. Der Dienst verwendet „Cookies“ – Textdateien, welche auf Ihrem Endgerät gespeichert werden. Die durch die Cookies gesammelten Informationen werden im Regelfall an einen Google-Server in den USA gesandt und dort gespeichert. Ggfs. wird Google Analytics auf dieser Webseite um den Code „gat._anonymizeIp();“ erweitert genutzt, um eine anonymisierte Erfassung von IP-Adressen (sog. IP-Masking) zu gewährleisten. Bitte beachten Sie auch die nachfolgenden Informationen zum Einsatz von Google Analytics: Die IP-Adresse der Nutzer wird innerhalb der Mitgliedsstaaten der EU und des Europäischen Wirtschaftsraum gekürzt. Durch diese Kürzung entfällt der Personenbezug Ihrer IP-Adresse. Im Rahmen der Vereinbarung zur Auftragsdatenvereinbarung, welche die Websitebetreiber mit der Google LLC geschlossen haben, erstellt diese mithilfe der gesammelten Informationen eine Auswertung der Websitenutzung und der Websiteaktivität und erbringt mit der Internetnutzung verbundene Dienstleistungen.
Rechtsgrundlage
Die Rechtsgrundlage für die Nutzung ist die Norm des Art. 6 Abs. 1 lit. a) DSGVO i.V.m. Art. 49 Abs. 1 lit. a) DSGVO, falls die anonymisierte Datenerfassung mittels des Codes “gat._anonymizeIp†nicht stattfindet. Ansonsten, insbesondere im Fall des Einsatzes von “gat._anonymizeIp†ist Art. 6 Abs. 1 lit. f) DSGVO die Rechtsgrundlage.
Empfänger
Im Falle der Aktivierung der IP-Anonymisierung auf dieser Webseite, wird Ihre IP-Adresse von Google jedoch innerhalb von Mitgliedstaaten der Europäischen Union oder in anderen Vertragsstaaten des Abkommens über den Europäischen Wirtschaftsraum zuvor gekürzt. Die durch den Cookie erzeugten Informationen über Ihre Benutzung dieser Website werden in der Regel an einen Server von Google in den USA übertragen und dort gespeichert. Nur in Ausnahmefällen wird die volle IP-Adresse an einen Server von Google in den USA übertragen und dort gekürzt. Im Auftrag des Betreibers dieser Website wird Google diese Informationen benutzen, um Ihre Nutzung der Website auszuwerten, um Reports über die Websiteaktivitäten zusammenzustellen und um weitere mit der Websitenutzung und der Internetnutzung verbundene Dienstleistungen gegenüber dem Websitebetreiber zu erbringen. Zusätzlich nutzen wir im Zusammenhang mit Google Analytics das Google Conversion Tracking. Dies ermöglicht uns das Verhalten von unseren Webseitenbesucher zu erfassen. Zum Beispiel wird uns angezeigt, wie viele PDFs auf unserer Webseite gedownloadet oder wie oft das Kontaktformular ausgefüllt wurde. Ebenso wird uns angezeigt, wie viele Klicks auf Werbeanzeigen von externen Quellen (AdWords, LinkedIn, Xing, Facebook, Pinterest, Instagram usw.) auf unsere Webseite geführt haben. Die im Rahmen von Google Analytics von Ihrem Browser übermittelte IP-Adresse wird nicht mit anderen Daten von Google zusammengeführt. Sie können die Speicherung der Cookies durch eine entsprechende Einstellung Ihrer Browser-Software verhindern; wir weisen Sie jedoch darauf hin, dass Sie in diesem Fall gegebenenfalls nicht sämtliche Funktionen dieser Website vollumfänglich werden nutzen können. Sie können darüber hinaus die Erfassung der durch das Cookie erzeugten und auf Ihre Nutzung der Website bezogenen Daten (inkl. Ihrer IP-Adresse) an Google sowie die Verarbeitung dieser Daten durch Google verhindern, indem Sie das unter dem folgenden Link (https://tools.google.com/dlpage/gaoptout?hl=de) verfügbare BrowserPlugin herunterladen und installieren.
Ãœbermittlung an Drittstaaten
Die Daten werden an einen Server von Google in den USA übertragen und dort gespeichert. Die personenbezogenen Daten werden auf Grundlage des Art. 46 und/oder Art. 49 Abs. 1 lit. a) DSGVO übermittelt.
Dauer der Datenspeicherung
Die von uns gesendeten und mit Cookies, Nutzerkennungen (z. B. User-ID) oder Werbe-IDs verknüpften Daten werden nach 14 Monaten automatisch gelöscht. Die Löschung von Daten, deren Aufbewahrungsdauer erreicht ist, erfolgt automatisch einmal im Monat.
Widerrufsmöglichkeit
Sie können die Speicherung der Cookies durch eine entsprechende Einstellung Ihrer Browser-Software verhindern; wir weisen Sie jedoch darauf hin, dass Sie in diesem Fall gegebenenfalls nicht sämtliche Funktionen dieser Website vollumfänglich werden nutzen können. Sie können darüber hinaus die Erfassung der durch das Cookie erzeugten und auf Ihre Nutzung der Website bezogenen Daten (inkl. Ihrer IP-Adresse) an Google sowie die Verarbeitung dieser Daten durch Google verhindern, indem Sie das Browser-Add-on herunterladen und installieren. Opt-Out-Cookies verhindern die zukünftige Erfassung Ihrer Daten beim Besuch dieser Website. Um die Erfassung durch Universal Analytics über verschiedene Geräte hinweg zu verhindern, müssen Sie das Opt-Out auf allen genutzten Systemen durchführen. Wenn Sie hier klicken, wird das Opt-Out-Cookie gesetzt: Google Analytics deaktivieren
Vertragliche oder gesetzliche Pflicht
Die Bereitstellung der personenbezogenen Daten ist weder gesetzlich noch vertraglich vorgeschrieben und auch nicht für einen Vertragsabschluss erforderlich. Sie sind auch nicht verpflichtet, die personenbezogenen Daten bereitzustellen. Die Nichtbereitstellung hätte jedoch unter Umständen zur Folge, dass Sie diese Funktion unserer Webseite nicht bzw. nicht vollumfänglich nutzen können.
Weitere Datenschutzhinweise via Link
Weitergehende Informationen zu Nutzungsbedingungen und Datenschutz finden Sie unter:
https://policies.google.com/?hl=de&gl=del
https://policies.google.com/privacy?hl=de&gl=de
Ich meine, wenn wir schon jemandem aus den USA vertrauen, dann doch sicherlich Google, deren Motto ja auch „don’t be evil“ ist (/war)?
Nö, danke, da interessiert mich dann der eigentliche Versand schon gar nicht mehr.
Wenn man mich vor Gericht als IT-Sachverständigen laden würde, um hier technisch zu erklären das es dennoch voll datenschutzkonform ist… ich müßte ablehnen.
Aber vielleicht guck ich mir die Versand-Infrastruktur doch noch mal an…


